Exploring the Effects of Ransomware on the Operations and Security of …
페이지 정보
작성자 Agnes Baughman 작성일24-09-02 06:17 조회16회 댓글0건관련링크
본문

In recent years, a notable shift has occurred in the realm of digital threats. Organizations that trade in information have found themselves increasingly targeted by malicious entities. These attacks often leave significant repercussions on operations and customer trust. The landscape is changing rapidly, and the stakes have never been higher.
Entities engaged in information exchange face a precarious balance between profit and security. Breaches not only jeopardize sensitive aspects of their business but also expose vulnerabilities previously overlooked. In the pursuit of safeguarding their assets, many have underestimated the severity of these threats. Consequently, the consequences of such intrusions can ripple throughout the entire industry.
Moreover, a profound sense of urgency has emerged among these information vendors. They must now respond swiftly to a fluctuating environment where risks multiply day by day. With each incident, lessons are learned, although often at a staggering cost. In seeking protective measures, organizations begin to realize the importance of not just technology, but also comprehensive strategies that address both prevention and recovery.
Undoubtedly, the interplay between cyber security measures and business continuity planning has taken center stage. As organizations navigate these turbulent waters, they must remain vigilant. Awareness, adaptation, and resilience have become key components of long-term strategies. Only by embracing these concepts can they hope to thrive in a landscape fraught with peril.
The Impact of Ransomware on Data Brokers
A surge in malicious attacks targeting organizations has created a significant shift in the landscape of digital security. Firms that specialize in collecting and selling information face unique challenges. They must navigate a minefield of threats that evolve constantly. Such risks not only jeopardize their operations but also raise serious concerns regarding client trust and data integrity.
With businesses increasingly reliant on information, vulnerabilities become more pronounced. A single breach can have cascading effects. For instance, a compromised system can lead to substantial financial losses, regulatory scrutiny, and long-term reputational damage. As these firms gather a vast array of sensitive information, they inadvertently become prime targets for cybercriminals.
Many professionals underestimate the severity of this growing menace. It’s not just about losing files or downtime; it's about the repercussions that ripple throughout the entire organization. Attackers often exploit weaknesses, locking crucial assets behind paywalls. This creates a critical dilemma: to comply or resist? The choices made in the heat of the moment can define a company's future.
Furthermore, it’s essential to recognize that recovery from such incidents can be arduous. Organizations may find themselves in an endless cycle of remediation, trying to patch vulnerabilities while facing constant threats. Each incident can trigger a wave of legal implications as affected parties seek accountability. Therefore, the stakes are exceedingly high, necessitating vigilance and proactive measures.
Industry leaders must prioritize robust shielding strategies. Training employees, establishing clear protocols, and investing in advanced technologies become non-negotiable. Additionally, sharing intelligence within the sector can fortify defenses against upcoming threats. Only through collaboration can firms hope to stay one step ahead of malevolent actors.
Understanding Ransomware Threats
In today's digital landscape, malicious attacks are increasingly common. This situation poses serious challenges for organizations and individuals alike. Many are unprepared for the sophistication of these threats. Awareness is crucial in combating such risks that can lead to devastating consequences.
To illustrate, various tactics are employed by cybercriminals to infiltrate systems. They exploit vulnerabilities, often hiding their actions until it’s too late. Targets are typically chosen based on their perceived value and susceptibility. This leads to a rise in the number of incidents affecting sensitive information.
Victims of these attacks face not only immediate disruption but also long-term repercussions. Therefore, understanding how these threats operate is vital for anyone involved in technology management.
- Techniques used for infiltration
- Common targets of these attacks
- Potential consequences for victims
- Indicators of a security breach
Techniques vary greatly, with phishing being a prevalent method. Unsuspecting users may unknowingly download harmful software. This often leads to loss of critical files and financial demands. Organizations must recognize common indicators, such as unexpected system behavior or unusual network traffic.
- Phishing emails that appear legitimate
- Unexpected pop-up messages requesting sensitive information
- Slow performance of computer systems
These signs require immediate attention, as delays can exacerbate the situation. Moreover, understanding the motivations behind these intrusions can help organizations bolster their defenses.
Many perpetrators are driven by profit. They see vulnerabilities in the systems as opportunities. Others, however, may have different motives. Some are driven by political agendas or simply seek chaos. This intricate web of intentions makes devising effective countermeasures particularly challenging.
Ultimately, knowledge is power when it comes to navigating this treacherous terrain. Regular training and updates regarding security protocols are essential. Investing in technology solutions can also provide an added layer of protection. Without proper precautions, the consequences can be severe, leading to financial losses and reputational damage.
Role of Data Brokers in Cybersecurity
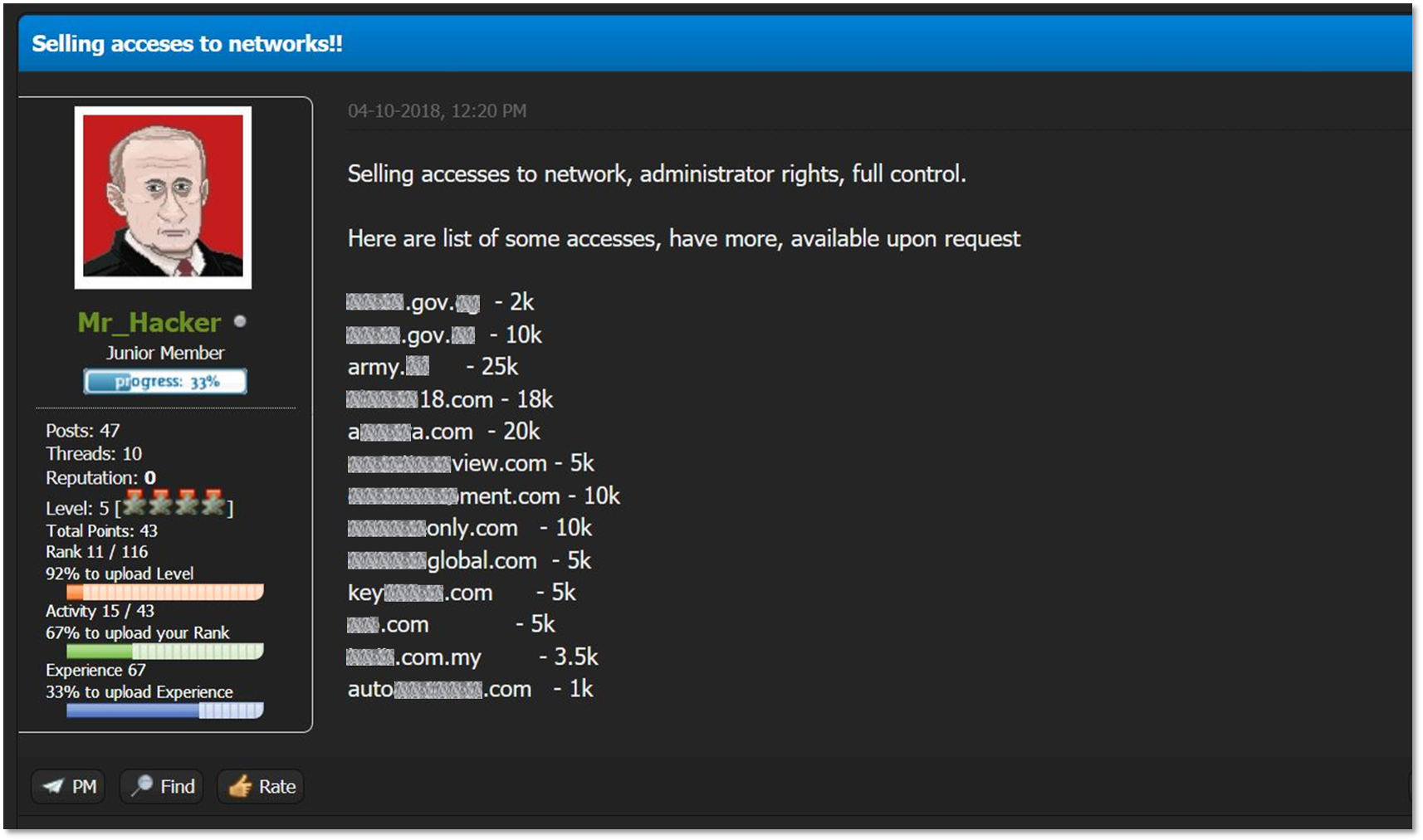
In today's digital landscape, entities involved in information exchange play a crucial role. They serve as intermediaries, collecting, analyzing, and distributing vast amounts of consumer details. These operations can be beneficial, but they also present significant challenges. Protecting sensitive information is more critical now than ever. Individuals and organizations rely on these services for insights, but risks abound.
Cybersecurity threats are pervasive and evolving continuously. Therefore, understanding how these intermediaries function in this environment is essential. Entities involved in information aggregation must adopt robust security measures to safeguard their assets. The relationship between these information custodians and cybersecurity is complex yet integral. As data flows through various networks, the potential for exploitation increases exponentially.
Many organizations often underestimate their vulnerabilities. They believe that simply relying on advanced technology is enough. However, the human element remains a significant factor in any security strategy. Without proper training and awareness, even sophisticated systems can be breached. Thus, investing in employee education and awareness programs is vital.
Prevention is always better than cure. By identifying potential threats early on, these entities can implement countermeasures effectively. Risk assessments should become a regular part of operations. Many firms are beginning to embrace proactive strategies as a means to stay ahead.
| Key Challenges | Proactive Measures |
|---|---|
| Data Breaches | Regular Security Audits |
| Insider Threats | Employee Training Programs |
| Compliance Issues | Implementing Best Practices |
| Technological Vulnerabilities | Up-to-Date Software |
In addition, establishing clear protocols for incident response is vital for mitigating damage. When breaches occur, timely and effective communication can significantly reduce repercussions. Entities must prepare for unexpected events by maintaining transparency with stakeholders. Innovation in cybersecurity practices can also provide a competitive edge. Hence, these intermediaries must continually adapt to safeguard against emerging threats.
Maintaining trust with clients and consumers hinges on effective information management. Organizations that prioritize security often enjoy enhanced reputations. This reinforces their value in the marketplace, creating a win-win scenario for everyone involved. As scrutiny from regulatory bodies intensifies, compliance becomes paramount. Ultimately, these operators must balance their objectives while ensuring the utmost protection of sensitive material.
Ransomware: A Growing Concern for Businesses
In recent years, the rise of malicious software aimed at extorting organizations has become a significant issue. This trend poses challenges not only to individual companies but also to entire industries. Businesses of all sizes face increasing threats as cybercriminals develop more sophisticated techniques. Various sectors remain vulnerable, often underestimating the potential consequences.
The consequences can be severe and multifaceted. Companies may experience financial losses, reputational damage, and disruptions to operations. In addition, the cost of recovery often spirals opt out from White Pages online of control, leading to unforeseen liabilities. Executives must understand that ignoring these risks is no longer an option. A single attack can compromise sensitive information, leading to legal ramifications and loss of customer trust.
Furthermore, organizations may find themselves in a predicament with regulators. Fines and penalties can compound financial troubles, making recovery even more daunting. Cyber insurance may mitigate some losses, but it cannot cover all aspects of the fallout. As a result, firms are compelled to rethink their entire approach to cybersecurity.
Moreover, many firms fail to recognize that recovery efforts extend beyond just technology. It involves revisiting policies, procedures, and employee training. Human error remains a critical factor in many breaches, emphasizing the need for comprehensive education. A robust strategy should encompass all aspects of a business’s operation to effectively safeguard against potential threats.
As this issue continues to escalate, stakeholders must stay informed and proactive. Engaging with cybersecurity professionals is vital for developing effective defense mechanisms. Investing in advanced technologies can help identify vulnerabilities before they can be exploited. Ultimately, adopting a culture of security awareness is essential for long-term success and stability.
Financial Consequences for Data Brokers
When cybercriminals target information aggregators, the financial fallout can be significant. These incidents often result in immediate monetary losses and long-term repercussions. For organizations in this sector, the stakes are exceedingly high. A breach can lead to not only theft of sensitive information but also a destabilization of trust with clients.
Investments in security infrastructure can soar. Companies must allocate resources for incident response teams. Legal fees can accumulate quickly if affected parties pursue litigation. Additionally, businesses may face hefty fines from regulatory authorities for failing to protect sensitive information.
- Immediate loss of revenue due to service disruption.
- Costs associated with recovery efforts and restoring systems.
- Potential penalties from regulatory bodies for non-compliance.
- Long-term damage to brand reputation leading to decreased client acquisition.
- Increased insurance premiums as risk profiles elevate.
Furthermore, even after addressing a breach, organizations may experience a decline in new business opportunities. Clients may choose to work with competitors perceived as more secure. This shift not only diminishes future earnings potential but also poses a challenge for retaining existing relationships.
Past cases highlight the severity of these financial ramifications, emphasizing the notion that proactive security measures can save organizations from catastrophe. Companies that have fallen victim to such attacks often see their market positions erode swiftly, leading to a crisis that is challenging to navigate.
- Invest in cybersecurity training for employees to prevent human error.
- Conduct regular audits of security practices and systems.
- Engage with third-party cybersecurity experts for assessments.
- Develop a comprehensive incident response plan for swift action.
Ultimately, the financial toll of a breach extends far beyond immediate losses. The need for comprehensive insurance coverage becomes evident. As the landscape of threats evolves, maintaining effective risk management strategies remains essential for ensuring long-term viability in a competitive market.
Case Studies: Ransomware Attacks on Brokers
Exploring real-world incidents sheds light on significant challenges within this sector. Understanding specific events helps illustrate broader vulnerabilities. Not all attacks are the same. However, the consequences can be devastating. Each case study reveals unique tactics employed by cybercriminals.
- High-Profile Incident A: In 2020, a major player fell victim to a serious breach. Attackers locked essential files and demanded payment. Operations were severely disrupted, leading to substantial financial losses. The company faced severe reputational damage as clients lost trust.
- Incident B: Another firm experienced a coordinated attack that targeted sensitive client information. After gaining access, hackers encrypted systems, hindering service delivery. Prolonged downtime resulted in irate customers and financial penalties. Recovery efforts took months, straining resources significantly.
- Incident C: A small outfit thought it was immune to such threats. Unfortunately, complacency proved costly. They were caught off guard when an attack paralyzed their infrastructure. This highlights how even smaller organizations are not exempt from cyber threats.
Through analyzing these examples, patterns begin to emerge, illustrating common tactics and points of weakness. Cybercriminals often exploit unpatched vulnerabilities or human error. Regular training and stronger security measures are essential to mitigate risks. Inadequate preparation can lead to devastating outcomes for any organization.
Ultimately, these incidents serve as cautionary tales, emphasizing the necessity for robust security frameworks. Advanced technologies can bolster defenses but must be coupled with vigilant human oversight. Regular assessments and updates to security protocols are vital for resilience. A proactive approach can make all the difference in safeguarding valuable information.
These case studies provide critical lessons learned for stakeholders across the board. Continuous vigilance remains key in an ever-evolving threat landscape. Fostering a culture of security awareness is paramount for all employees. Collective efforts can significantly reduce vulnerability and deter potential attacks.
Preventative Measures for Data Security
Ensuring security involves a multifaceted approach that encompasses various strategies and tools. Organizations today face numerous threats. Being proactive is crucial. Developing a robust framework can shield sensitive information from unwanted access and breaches. This section will explore vital practices that can significantly enhance the resilience of systems.
First and foremost, conducting regular risk assessments is essential. Identifying vulnerabilities allows for timely action. It helps organizations understand potential weaknesses in their infrastructure. This understanding lays the foundation for effective security measures. Consequently, prioritizing areas that require immediate attention is key to maintaining integrity.
Another critical step is implementing strong access controls. Limiting access to essential personnel ensures that sensitive information remains within trusted hands. Therefore, using multi-factor authentication is highly recommended. It adds an extra layer of verification that can deter unauthorized users. Additionally, ensuring that employees receive training on security best practices cannot be overlooked.
Utilizing advanced encryption methods protects information during transmission and storage. Encryption transforms readable data into an unreadable format, making it inaccessible without the correct decryption key. Hence, even if sensitive information falls into the wrong hands, it remains impenetrable. This practice is vital for organizations that handle confidential client information.
Collaboration with cybersecurity experts is an excellent strategy. Engaging with specialists equips organizations with the latest knowledge and tools. Consequently, they can better prepare for emerging threats. Regular updates to software and systems play a crucial role too. Keeping everything up-to-date ensures that any discovered vulnerabilities are promptly addressed.
| Preventative Measure | Description |
|---|---|
| Risk Assessments | Identifying and analyzing vulnerabilities in systems. |
| Access Controls | Restricting access to sensitive information. |
| Encryption | Securing information by transforming it into an unreadable format. |
| Employee Training | Educating staff on best practices for security. |
| Software Updates | Regularly updating systems to address vulnerabilities. |
In conclusion, safeguarding sensitive information requires a holistic strategy. Organizations must be vigilant and proactive in their approaches. By implementing robust measures, they can significantly reduce the risk of a breach. Investing time and resources into security enhances integrity. In this digital age, prioritizing cybersecurity is not merely an option; it is a necessity.
Regulatory Responses to Ransomware Incidents
In recent years, a significant shift has occurred in how authorities approach threats to digital security. Organizations, large and small, face challenges from malicious attacks that can cripple operations. As a result, regulatory bodies are increasingly stepping up to address these pressing issues. This change reflects a growing recognition of the need for protective measures and proactive strategies. It's not just about responding anymore; it’s about creating frameworks for resilience.
Legislation has begun to evolve alongside these emerging threats. New guidelines and standards have been introduced to help organizations safeguard their networks. Compliance with these regulations has become essential for businesses. Failure to adhere to them can lead to severe penalties. Furthermore, agencies are now emphasizing collaboration between sectors.
Many governments have established task forces that focus on cybersecurity education and awareness. These groups aim to bridge gaps in knowledge and practice, making it easier for companies to understand their risks. Furthermore, enhancing reporting requirements ensures that incidents are documented and analyzed effectively. This data can inform future regulations and help guide best practices.
In addition to compliance, there is a push for transparency. Stakeholders want to know how organizations handle incidents and what steps are taken afterward. This openness fosters trust and prepares the community for potential threats. Enhanced communication between companies can lead to a robust collective defense mechanism.
Regulatory frameworks are not only about compliance; they also serve as a guide for best practices. They encourage organizations to take a proactive stance. Investing in security infrastructure is now seen as a necessity rather than an option. Risk management strategies have become a focal point, emphasizing the importance of resilience in the face of attacks.
Ultimately, moving forward, businesses will need to remain agile. As rules change, so too must strategies for implementation. Continuous reassessment of policies will be crucial. By staying ahead of trends, companies can ensure they are not only compliant but also prepared for unforeseen challenges. The landscape is shifting, and adaptation is key to survival in this digital age.
The Future of Data Handling Practices
With the evolution of threats and technological advancements, approaches to managing sensitive information must adapt. Organizations are increasingly recognizing that safeguarding their assets goes beyond mere compliance. It requires a proactive mindset, leading to innovative methodologies and frameworks. This shift is crucial in today's digital landscape, where vulnerabilities can be exploited at any moment.
Emerging practices will likely focus on several key areas:
- Enhanced encryption techniques for securing information.
- Integration of artificial intelligence to predict and mitigate risks.
- Regular audits and assessments to identify weaknesses.
- Increased training and awareness programs for employees.
Incorporating advanced technologies is becoming essential. Utilizing machine learning enables organizations to analyze patterns and detect anomalies effectively. Simultaneously, training staff ensures that everyone is aware of potential threats. This strategy not only fosters a culture of security but also empowers individuals to act swiftly when challenges arise.
- Develop a robust incident response plan.
- Establish a framework for continuous improvement.
- Collaborate with industry peers to share intelligence.
- Invest in research to stay ahead of emerging threats.
As businesses navigate this complex terrain, regulatory environments are also evolving. Compliance frameworks will likely become tighter, enforcing stricter guidelines for best practices. As such, organizations must remain agile, adapting their policies to meet new demands. The interplay between compliance and innovative practices creates a dynamic landscape for managing sensitive information.
Ultimately, the goal is clear: foster a resilient infrastructure capable of withstanding various threats. This focus on resilience not only protects valuable assets but also builds trust with clients and stakeholders. As we move forward, embracing these changes will be paramount. Organizations that prioritize innovative strategies will not only thrive but also set the standard for others in their industry.
Best Practices for Risk Mitigation
Ensuring the safety of sensitive information is critical in today’s digital landscape. Organizations must adopt a proactive approach to protect themselves. Implementing effective strategies can greatly reduce vulnerabilities. Awareness and continuous improvement are key elements in this process.
Regular training for employees is essential. Staff should understand potential threats and appropriate responses. Fostering a culture of vigilance can make a significant difference. Everyone within the organization plays a role in safeguarding information.
Utilization of advanced security technologies cannot be overlooked. Firewalls, intrusion detection systems, and encryption tools provide strong layers of defense. By employing these technologies, businesses enhance their protective measures. However, technology alone is not sufficient without robust human oversight.
Conducting frequent risk assessments helps identify weaknesses. This ongoing evaluation allows for timely adjustments to security protocols. Understanding evolving threats equips organizations to respond effectively. Staying updated on the latest intelligence ensures resilience against emerging challenges.
Additionally, maintaining comprehensive backup solutions is vital. Regularly updated backups can act as a lifeline in case of an incident. These backups should be stored securely, ideally in multiple locations. This redundancy minimizes potential data loss and aids in swift recovery.
Establishing an incident response plan is another crucial aspect. Such a plan outlines specific actions in the event of a security breach. Clear protocols streamline communication and decision-making, facilitating a quicker resolution. Moreover, testing the plan through simulations prepares teams for real-world scenarios.
Creating strong access controls is equally important. Limiting user permissions to only what is necessary reduces exposure to risks. Regularly review and adjust access settings to reflect current needs. A meticulous approach to access management strengthens overall security posture.
Finally, fostering collaboration with external experts can enhance protection strategies. Engaging with cybersecurity professionals provides valuable insights. Their expertise helps businesses stay one step ahead of potential threats. When organizations prioritize safety, they pave the way for sustainable operations.
댓글목록
등록된 댓글이 없습니다.









